RAID Log in Project Management: When, Why, and How to Use It for Stakeholder Updates
Discover how to use a RAID log in project management for better stakeholder updates, risk management, and decision-making.
Effective stakeholder communication is a cornerstone of successful project management. One of the most powerful tools for keeping stakeholders informed and aligned is the RAID Log in Project Management. By systematically tracking risks, assumptions, issues, and dependencies, the RAID log helps project managers provide transparent, organized updates. This ensures that stakeholders are kept in the loop, potential problems are addressed early, and decisions are made based on a clear understanding of the project’s current status.
In this article, we’ll explore when and why you should use a RAID log for stakeholder updates, along with practical tips on how to implement it successfully.
Before diving into the details of the RAID log, explore our article about what is project management to gain deeper insight into the context and principles that make the RAID log an essential tool for project success.
What Is a RAID Log?
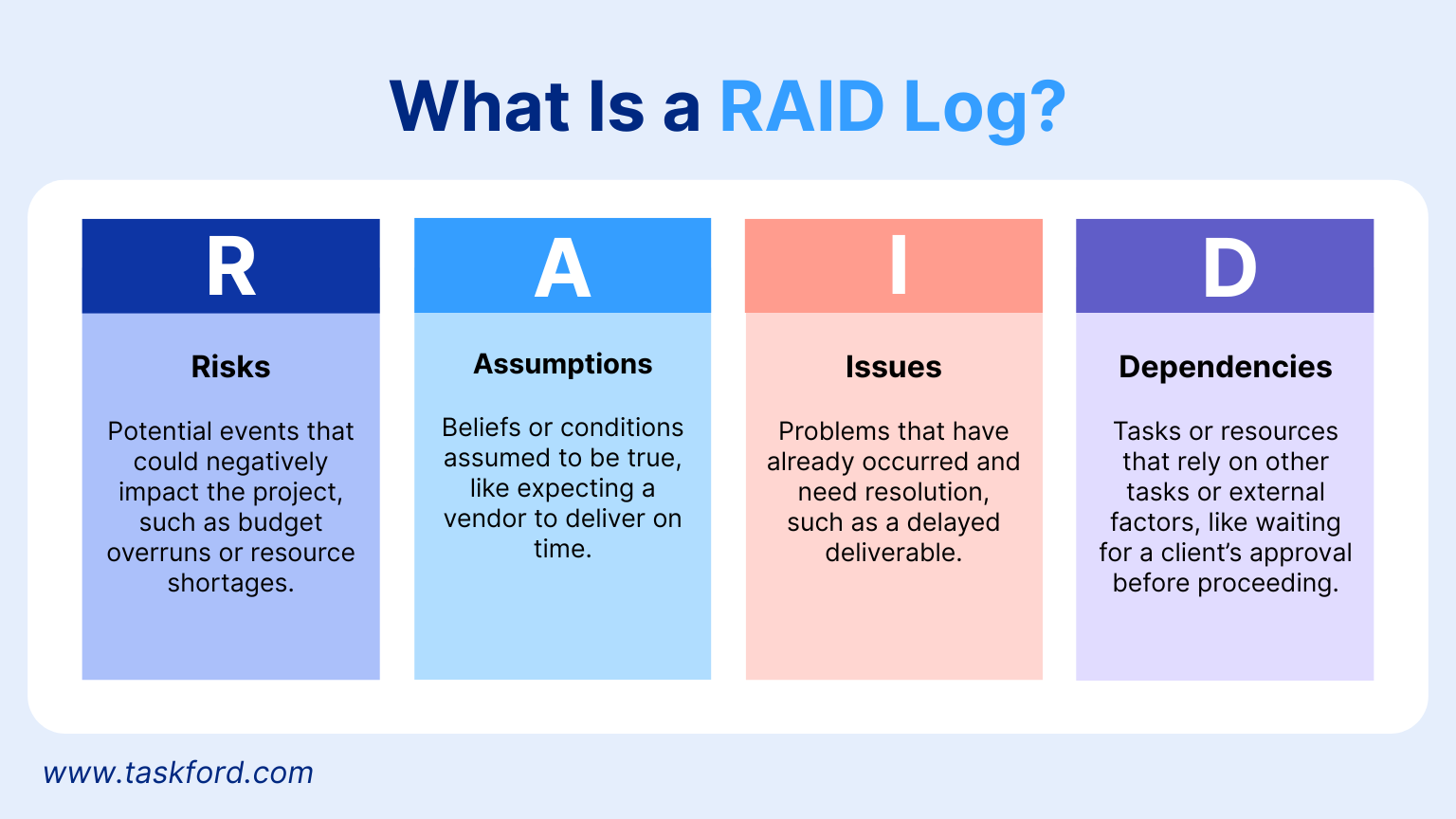
A RAID log is a document or spreadsheet used in project management to monitor four key components: Risks, Assumptions, Issues, and Dependencies. Each component plays a distinct role in ensuring project success:
- Risks: Potential events that could negatively impact the project, such as budget overruns or resource shortages.
- Assumptions: Beliefs or conditions assumed to be true, like expecting a vendor to deliver on time.
- Issues: Problems that have already occurred and need resolution, such as a delayed deliverable.
- Dependencies: Tasks or resources that rely on other tasks or external factors, like waiting for a client’s approval before proceeding.
The RAID log centralizes these elements, making it easier to track and report on them.
When to Use a RAID Log
A RAID log is useful throughout the project lifecycle, but its application depends on the phase and context. Here’s when it’s most effective:
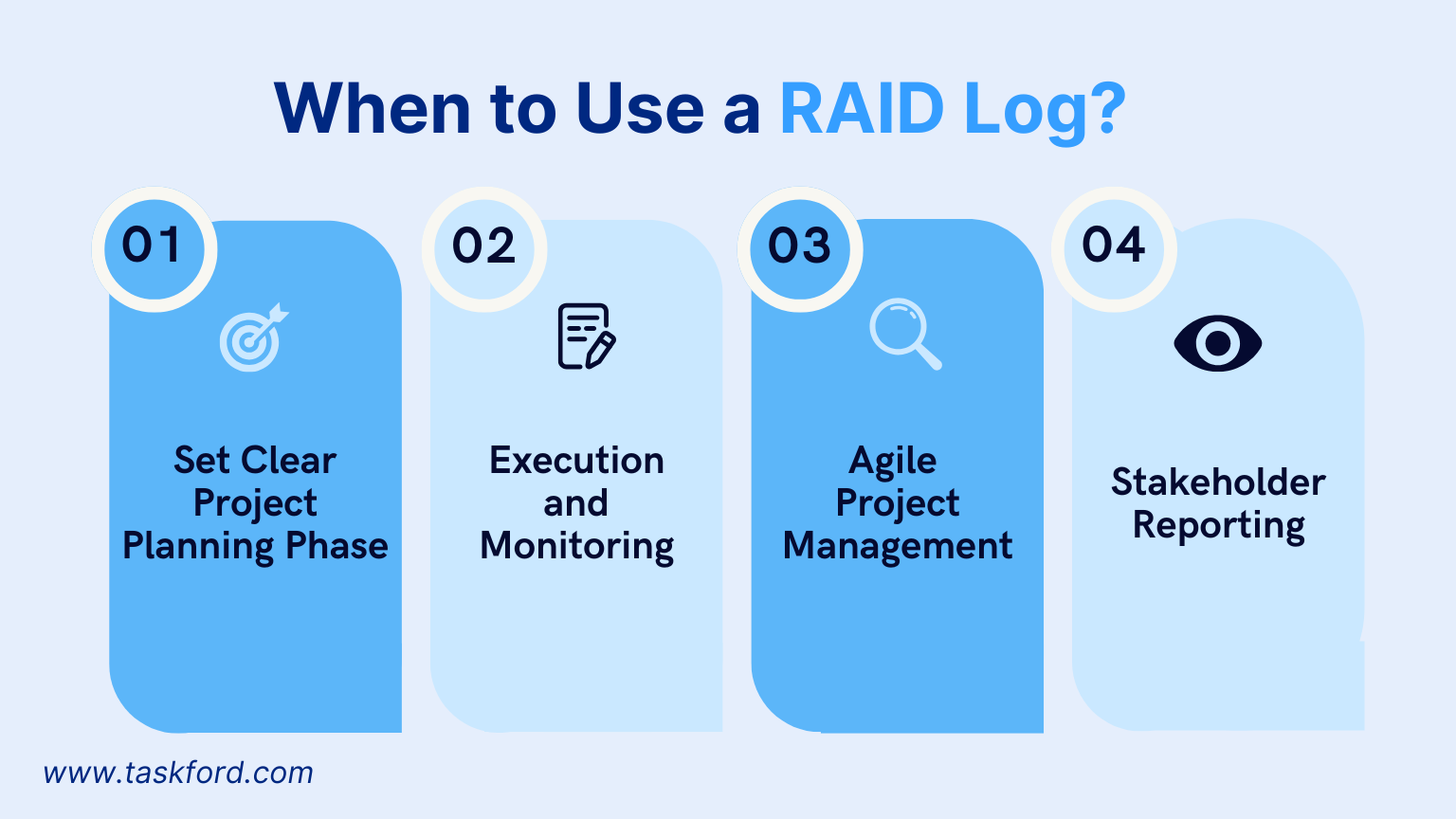
1. Project Planning Phase
During planning, the RAID log helps identify potential risks and dependencies early. For example, you might note a risk of scope creep or a dependency on a third-party vendor. Documenting assumptions, like stable team availability, also sets a foundation for realistic planning. Using tools like a Risk Assessment Matrix can complement the RAID log by prioritizing risks based on likelihood and impact.
2. Execution and Monitoring
As the project progresses, the RAID log tracks active issues and updates on risks or dependencies. Regular updates ensure stakeholders are informed about challenges, such as a delayed milestone, and how they’re being addressed. This phase is where the log’s value in stakeholder communication shines, as it consolidates critical updates.
3. Agile Project Management
In agile project management environments, where flexibility and iteration are key, the RAID log adapts to frequent changes. For instance, during sprint planning, teams can use it to flag new risks or dependencies that emerge. It aligns with agile principles by promoting transparency and collaboration, making it a versatile tool for agile project managers.
4. Stakeholder Reporting
When preparing for stakeholder meetings, the RAID log provides a structured way to present project status. Instead of overwhelming stakeholders with details, you can highlight key risks, issues, or dependencies that need their input or approval. This keeps discussions focused and productive.
Why a RAID Log Matters in Project Management

The RAID log is vital for keeping projects organized and on track. It helps project managers stay proactive and maintain clear communication. Here’s why it’s important:
- Centralizes Information: Consolidates risks, assumptions, issues, and dependencies, providing a clear overview without searching through scattered documents.
- Supports Proactive Risk Management: Tracks risks early, enabling mitigation plans, like addressing a potential vendor delay before it disrupts the project.
- Tracks Dependencies and Assumptions: Highlights dependencies that could stall progress and assumptions needing validation to avoid surprises.
- Ensures Accountability: Assigns owners to each item, keeping the team focused on resolving challenges.
- Improves Stakeholder Updates: Offers a concise project health snapshot, helping present key risks or issues for informed stakeholder decisions.
For example, a RAID log can track a potential budget overrun and a delayed deliverable, assign responsibilities, and outline mitigation plans, ensuring effective project oversight.
How to Create and Maintain a RAID Log Effectively for Stakeholder Updates
Creating a RAID log is straightforward, but maintaining it requires discipline. Below is a step-by-step guide to set up and use a RAID log effectively.
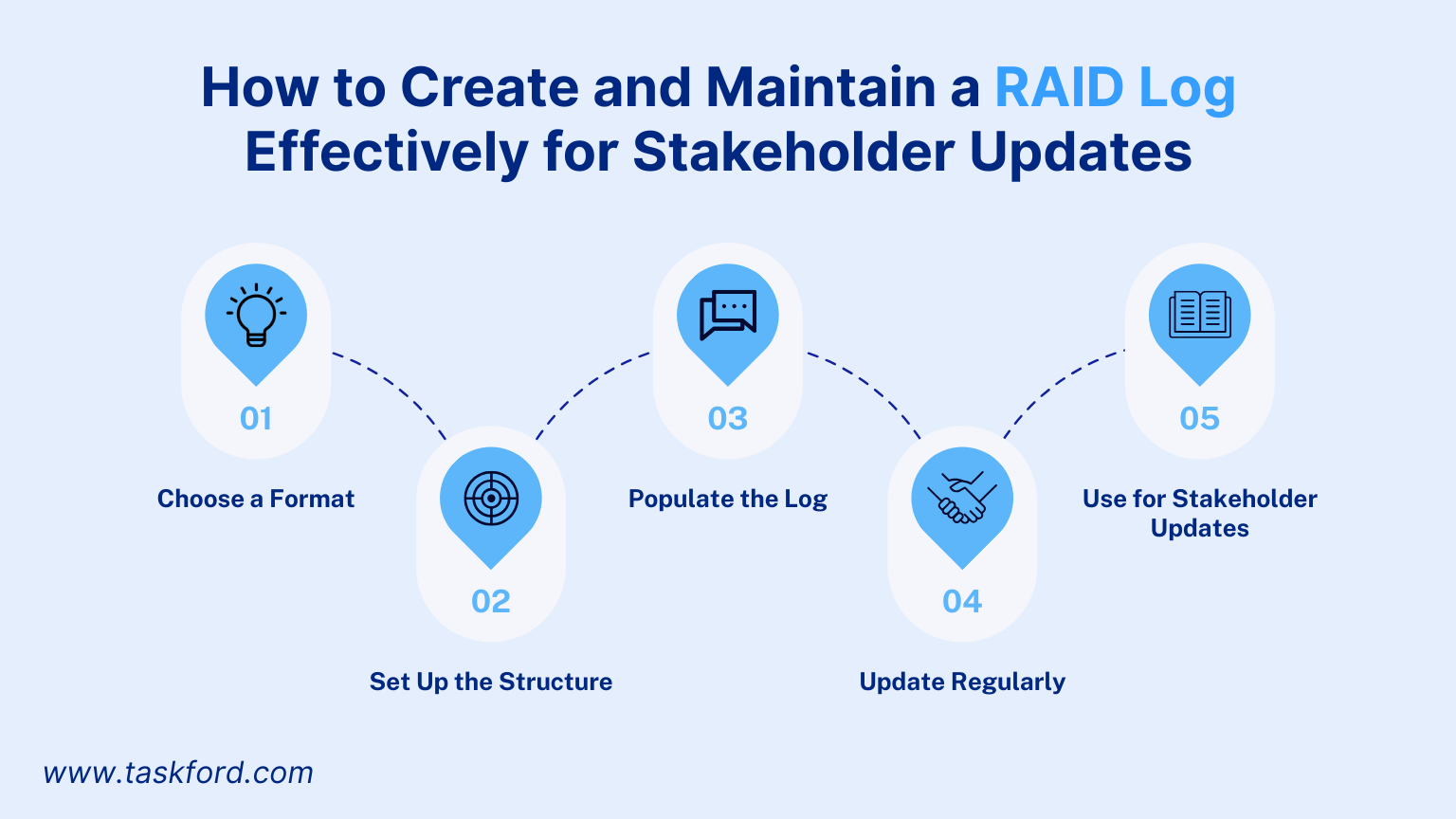
Step 1: Choose a Format
A RAID log can be a spreadsheet, a table in a project management tool, or a document. Spreadsheets are popular due to their flexibility and ease of sharing. Common tools include Microsoft Excel, Google Sheets, or software like Jira and Asana, which offer RAID log templates.
Step 2: Set Up the Structure
Divide the log into four sections: Risks, Assumptions, Issues, and Dependencies. Each section should include:
- ID: A unique identifier for tracking (e.g., R1 for Risk 1, I1 for Issue 1).
- Description: A brief explanation of the item.
- Impact: The potential or actual effect on the project (e.g., delay, cost increase).
- Owner: The person responsible for managing or resolving it.
- Status: Current state (e.g., open, in progress, resolved).
- Mitigation/Action Plan: Steps to address or monitor the item.
- Date Identified/Updated: When the item was added or last reviewed.
For risks, include additional columns like Likelihood and Severity to prioritize them, as outlined in our risk assessment matrix guide.
Step 3: Populate the Log
During planning, brainstorm with your team to identify risks, assumptions, and dependencies. For example:
- Risk: “Team member illness could delay development” (Likelihood: Medium, Severity: High).
- Assumption: “Client will provide feedback within three days.”
- Dependency: “Design phase completion depends on client approval.”
- Issue: “Server outage caused a two-day delay.”
Engage stakeholders or team members to ensure all perspectives are covered.
Step 4: Update Regularly
Review and update the RAID log at least weekly or during key project milestones. In agile projects, align updates with sprint cycles. Remove resolved issues or risks to keep the log concise, but archive them for future reference.
Step 5: Use for Stakeholder Updates
When preparing for stakeholder meetings, filter the RAID log to highlight items requiring their attention. For example, focus on high-priority risks or unresolved issues. Present the log in a summarized format, such as a table or bullet points, to make it digestible. Avoid overloading stakeholders with every detail—focus on what impacts their decisions.
Example RAID Log Table
| ID | Type | Description | Impact | Owner | Status | Action Plan | Last Updated |
|---|---|---|---|---|---|---|---|
| R1 | Risk | Vendor delay in software delivery | 2-week delay | J. Smith | Open | Negotiate expedited delivery | 06/20/2025 |
| A1 | Assumption | Team has required skills | Scope creep | T. Brown | Validated | Conduct training if needed | 06/15/2025 |
| I1 | Issue | Server outage delayed testing | 1-day delay | L. Davis | Resolved | Implemented backup server | 06/18/2025 |
| D1 | Dependency | Waiting on client design approval | Blocks next phase | M. Wilson | Open | Follow up with client by 06/25 | 06/19/2025 |
Best Practices for RAID Log Management
To maximize the RAID log’s value, follow these tips:
- Keep It Simple: Avoid overcomplicating the log with too many details. Focus on high-impact items that affect the project’s timeline, budget, or quality.
- Assign Clear Ownership: Every item in the RAID log should have an owner responsible for monitoring or resolving it. This ensures accountability and prevents items from being overlooked.
- Integrate with Agile Practices: In agile projects, incorporate the RAID log into sprint reviews or daily stand-ups. For example, discuss new risks during sprint planning to align the team’s focus.
- Communicate Proactively: Share the RAID log or its highlights with stakeholders regularly, not just when problems arise. This builds trust and keeps everyone aligned.
- Use Visual Aids: For stakeholder updates, consider visualizing key RAID log items using charts or dashboards. For instance, a risk heat map can highlight high-priority risks visually.
Final Thoughts
The RAID log goes beyond being just a documentation tool; it serves as a vital communication bridge between the project team and stakeholders. When used effectively, it enhances transparency, streamlines decision-making, and strengthens stakeholder trust by keeping everyone informed and aligned. By consistently updating and utilizing the RAID log, project managers can anticipate potential issues, manage risks, and ensure that all critical factors are addressed, ultimately contributing to the successful delivery of the project.
Subscribe for Expert Tips
Unlock expert insights and stay ahead with TaskFord. Sign up now to receive valuable tips, strategies, and updates directly in your inbox.